POS: Security Flaws allows hacker to change price, steal data
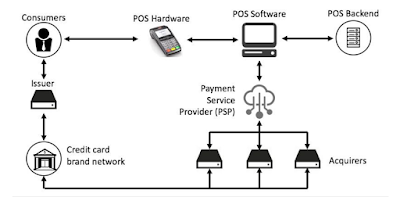
Researchers at ERPScan discovered that SAP’s POS product, that is a component of the company’s SAP for Retail giving, was stricken by many flaws. Specifically, the system’s server element, Xpress Server, lacked necessary authorization checks for vital practicality. This allows AN assailant with access to the system to send malicious configuration files to Xpress Server and gain complete management of each the frontend and backend of the PoS system. A hacker will abuse tens of commands, permitting them to steal knowledge from all the credit and debit cards used at the targeted store, and apply special costs and discounts to such that things. These discounts is applied for such that times in order that AN item contains a tiny value only fraudsters visit purchase it. Fraudsters may also got wind of the system in order that their purchases area unit charged to the previous customer’s card. An assailant may also modification the info displayed on a receipt, as well as to s