WikiLeaks - Vault7 : HighRise used for SMS monitoring
WikiLeaks has released details
about HighRise, a tool allegedly developed by the US- CIA, which intercepts and
redirects SMS messages to a remote web server through an Android application. The
malware can enable a CIA agent to access the message before it reaches its
intended recipient.
As per tweets of WikiLeaks,
HighRise acts as a proxy server for text messages. However, it is limited to
devices which have the malware installed on it manually – meaning that the CIA
would need physical access to the Android device to infect the handset.
The
manual suggested that it only works on Android versions from 4.0 (Ice Cream
Sandwich) to 4.3 (JellyBean) – although it could have been updated to work on
more recent versions of the Android OS.
The
HighRise tool is packaged inside an app called TideCheck. Once the CIA installs
the app on the target’s device, they have to run it at least once, in order for
it to work at all times – including when the phone is rebooted. The app starts
when the phone is powered on, meaning that it can continue to run in the
background and intercept text messages for longer than most other CIA malware,
which disappeared after a restart.
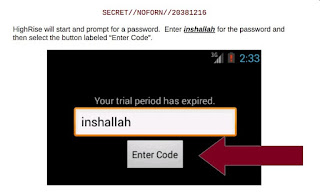
According
to the manual, CIA operatives have to enter the special code like password
‘inshallah’ which is the Arabic word for ‘God willing’ to access the app’s
settings.
Once
activated, the app gives the user three choices –
1) They can
return directly to the configuration to make changes,
2)
They can start the tool
3)
They can send an SMS from the phone to a remote CIA server.
This
is the first Vault 7 data dump to involve the Android OS; most of the other
tools have been focused on Windows or Linux. This included Grasshopper, a
builder for Windows malware, and Scribble, a beaconing system for Office
documents. There has also been a tool geared to hack Samsung smart TVs, and a
tool for hacking iPhones and Macs.
Read full Document Here.




Comments
Post a Comment