POS: Security Flaws allows hacker to change price, steal data
Researchers at ERPScan
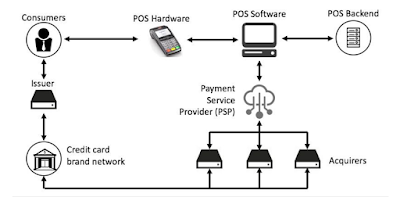
discovered that SAP’s POS product, that is a component of the company’s SAP for
Retail giving, was stricken by many flaws. Specifically, the system’s server
element, Xpress Server, lacked necessary authorization checks for vital practicality.
This allows AN assailant
with access to the system to send malicious configuration files to Xpress
Server and gain complete management of each the frontend and backend of the PoS
system.
A hacker will abuse tens
of commands, permitting them to steal knowledge from all the credit and debit
cards used at the targeted store, and apply special costs and discounts to such
that things. These discounts is applied for such that times in order that AN
item contains a tiny value only fraudsters visit purchase it. Fraudsters may
also got wind of the system in order that their purchases area unit charged to
the previous customer’s card.
An assailant may also
modification the info displayed on a receipt, as well as to show the customer’s
full payment card variety, not simply the last four digits as needed.
An attack needs access to
the targeted network. However, specialists recognized that thereforeme systems
area unit exposed to the net so remote attacks could also be potential. If the
PoS system isn't connected to the net, AN assailant might plant the malware
employing a Raspberry Pi device that's connected to the targeted store’s
network. ERPScan noted that the inner network will typically be accessed from
the electronic scales obtainable in stores.
Some technical details
were disclosed by ERPScan researchers during a presentation at the Hack within
the Box (HITB) security conference happening on in Singapore.
SAP, whose retail
solutions area unit employed by eighty p.c of the Forbes international 2000 retailers,
was informed concerning the
vulnerabilities in April and free a patch in Gregorian calendar month as a part
of its regular security updates. However, the corporate free another update on
August eighteen when researchers discovered that the initial fix may be
bypassed via a replacement flaw.
ERPScan researchers
recognized that these varieties of vulnerabilities don't seem to be specific to
SAP merchandise. they need conjointly found similar flaws in Oracle’s MICROS
system.
“Many POS systems have
similar design and therefore same vulnerabilities,” aforementioned ERPScan’s
Dmitry Chastuhin, one in every of the researchers United Nations agency found
the vulnerabilities. “POS terminals wont to be infested with vulnerabilities as
myriads of them were found and, sadly, exploited, therefore their security
posture has improved considerably. On the opposite hand, banks should adhere to
totally different compliance standards. So, the connections between POS digital
computer and also the store server prove to be the weakest link. They lack the
fundamentals of cybersecurity - authorization procedures and secret writing,
and no-one cares concerning it. So, once AN assailant is within the Network, he
or she gains full management of the system.”
Read Full white paper:


Comments
Post a Comment